Photo AI
Last Updated Sep 26, 2025
Encryption Simplified Revision Notes for GCSE OCR Computer Science
Revision notes with simplified explanations to understand Encryption quickly and effectively.
295+ students studying
Encryption
Encryption is the process of converting data into a coded form so that it cannot be understood if intercepted.
It ensures that sensitive information, such as passwords or financial details, is protected from unauthorized access. The data can only be decrypted and understood by someone who has the correct key.

Decryption: The process of converting encrypted data back to its original form using a key.
The Principle of Encryption to Secure Data
Encryption secures data as it travels across networks by scrambling it into an unreadable format. Even if the data is intercepted during transmission, it remains secure because the person intercepting it cannot understand it without the correct key. This is essential in protecting personal information and maintaining privacy over the internet, especially in activities like online banking, email communication, and file transfers.
Types of Encryption
Caesar Cipher
- A simple encryption technique where each letter in the message is shifted by a certain number of places in the alphabet.
- For example, shifting "A" by 3 would make it "D". It is easy to break but introduces the concept of encryption.
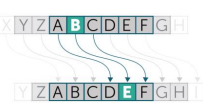
Symmetric Encryption
- The same key is used for both encrypting and decrypting the data.
- Both parties must have access to the secret key, making key management crucial.
- It's faster but less secure if the key is intercepted.
Public Key Encryption (Asymmetric Encryption)
- Uses two keys: a public key to encrypt the data and a private key to decrypt it.
- The public key is shared openly, but the private key is kept secret by the receiver.
- More secure since only the private key holder can decrypt the data.
Encryption for Wi-Fi Security
- WEP (Wired Equivalent Privacy) and WPA (Wi-Fi Protected Access) are common encryption methods used to secure Wi-Fi networks.
- WEP is older and less secure, while WPA and newer versions like WPA2 offer stronger encryption and better protection against unauthorized access to the network.
Key Points to Remember
- Encryption protects data by turning it into an unreadable format that only authorized parties can decrypt.
- Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of public and private keys.
- Modern Wi-Fi networks use encryption methods like WPA to secure wireless communications and prevent unauthorized access.
500K+ Students Use These Powerful Tools to Master Encryption For their GCSE Exams.
Enhance your understanding with flashcards, quizzes, and exams—designed to help you grasp key concepts, reinforce learning, and master any topic with confidence!
70 flashcards
Flashcards on Encryption
Revise key concepts with interactive flashcards.
Try Computer Science Flashcards7 quizzes
Quizzes on Encryption
Test your knowledge with fun and engaging quizzes.
Try Computer Science Quizzes10 questions
Exam questions on Encryption
Boost your confidence with real exam questions.
Try Computer Science Questions3 exams created
Exam Builder on Encryption
Create custom exams across topics for better practice!
Try Computer Science exam builder13 papers
Past Papers on Encryption
Practice past papers to reinforce exam experience.
Try Computer Science Past PapersOther Revision Notes related to Encryption you should explore
Discover More Revision Notes Related to Encryption to Deepen Your Understanding and Improve Your Mastery
96%
114 rated
Wired & Wireless Networks, Protocols & Layers
Modes of Connection
467+ studying
181KViews96%
114 rated
Wired & Wireless Networks, Protocols & Layers
IP Addressing & MAC Addressing
211+ studying
184KViews96%
114 rated
Wired & Wireless Networks, Protocols & Layers
Standards in Computing
216+ studying
187KViews96%
114 rated
Wired & Wireless Networks, Protocols & Layers
Network Protocols
496+ studying
199KViews